Product Page: https://www.jetico.com/data-encryption/encrypt-hard-drives-bestcrypt-volume-encryption
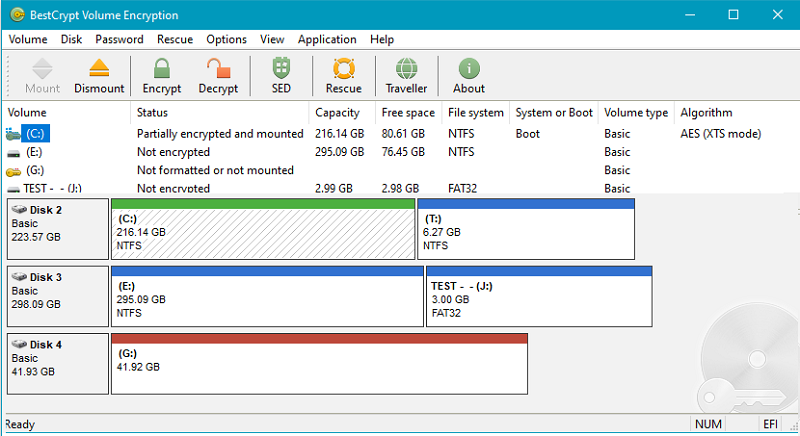
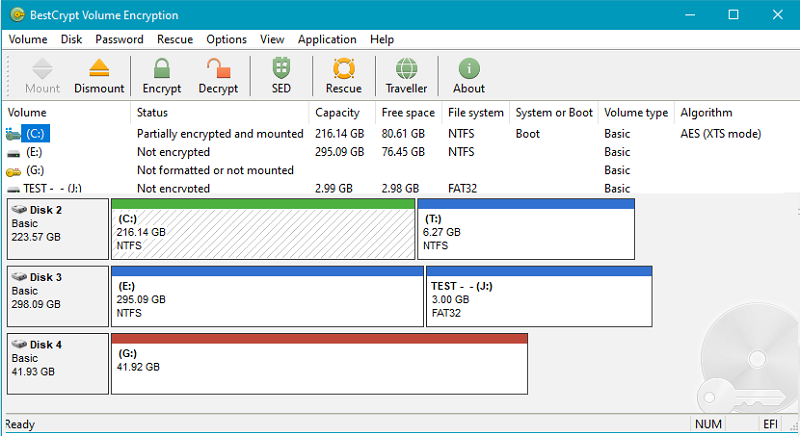
BestCrypt Volume for Disk Encryption protects all data on all types of volumes residing on fixed and removable disks – simple volumes, mount points, multipartition volumes (spanned, mirrored, striped, RAID-5), while also working on UEFI and GPT partitions. Jetico’s encryption software provides protection from physical threats – such as lost computers and USB sticks – to protect your privacy and comply with regulations (HIPAA, PCI). BestCrypt Volume Encryption utilizes a wide variety of algorithms (AES, Twofish, Serpent) and the largest possible key sizes with XTS, LRW encryption modes. By working with volumes, Jetico’s disk encryption is the best TrueCrypt alternative.
Disk encryption features:
– Encrypt system and boot volumes
– Support for UEFI-based computers, including secure boot
– Encrypt RAID and all types of volumes residing on fixed and removable disks
– Pre-boot authentication
– Support for Tokens for secure hardware storage of encryption keys
– Two-factor authentication with removable disk drives
– User-friendly encryption
– Option to boot encrypted volumes only from trusted network
– Support for Trusted Platform Module (TPM) for unattended reboot
– Secure hibernation
– Rescue functions to decrypt volumes in emergency case
– Central management for deployment, monitoring, encryption policy distribution and password recovery (Enterprise Edition only)